There are several protocols that must be followed when engaging in telecommuting and these standards are outlined by the National Institute of Standards and Technology (NIST). Employees must assume that external environments contain hostile threats and protect the information accordingly through secured telework devices such as flash drives, hard drives, computers, mobile devices, and more.
Both employees and administrators must enact proper security protocols to protect corporate data, which can include employee records, personally identifiable information on clients, and internal business practices that are targeted by competitors. Telecommuters work from a variety of places such as homes, coffee shops, hotels, and libraries. Being outside of an enterprise environment leaves devices more vulnerable to an attack, meaning there is a need for stronger security policies for data storage and transfer.
To keep a business secure while teleworking, privacy and caution must be an organization’s priority when working with digital devices. Follow these steps to protect corporate data while teleworking:
- Develop a telecommuting security policy with tiered levels of access
- Use anti-malware technologies and software on your devices
- Implement multi-factor authentication to access devices
- Have different and unique passwords to access both corporate-issued devices and personal telework media
- Encrypt data at rest as well as information that is being transferred between media
- Educate the workforce to obtain authorization from their supervisors before removing any data (in either paper or electronic format) containing PII from the workplace unless correctly secured.
- Keep track of security events and device access with proper logging policies
- Remove sensitive data from a telework device before the employee permanently leaves the organization
Why SecureDrives and SecureUSBs are the Ideal Telecommuting Tool
These hardware encrypted and FIPS 140-2 Level 3 Validated storage devices protect against every potential threat that comes with teleworking. The SecureDrives and SecureUSBs come with built-in antivirus to prevent files from corruption when being transferred from a remote worker’s computer to the storage device.
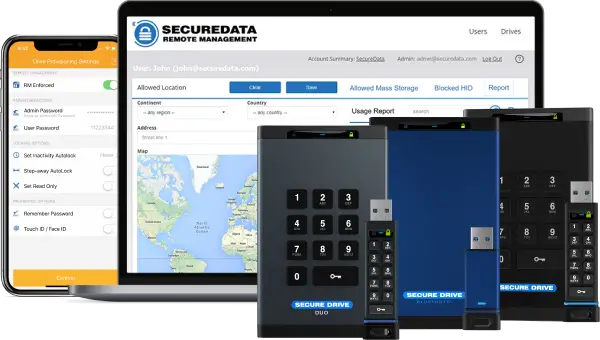
The SecureDrive and Secure USB BT offer two-factor authentication when accessing the drive through a secure mobile app. With the device’s remote management capabilities, a remote worker will only have access to the drive after the admin for the device allows it. The managers and administrators in a company will also have the ability to review access logs of when a device was used, when, and by whom. Additional features that accompany the remote management subscription are geo- and time-fencing to restrict drive access to predetermined times and places.
Both the BT and KP models of these secure storage devices have inactivity auto-lock to prevent unauthorized access to data if an employee is working in a public place. After an employee or admin leaves the company, the SecureDrive devices can be remotely wiped or data can be destroyed through brute force anti-hacking technology.